This issue in pdf Subscription Archive: Next issue: January 2006 |
|
|||||||
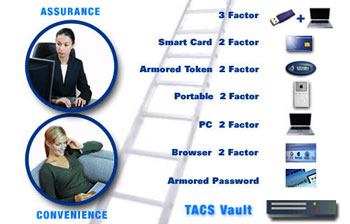
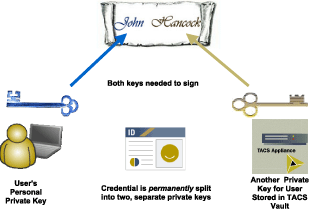
Flexible Multi-Factor Authentication in an Uncertain Worldby Ravi Sandhu Most organizations require high-grade multi-factor authentication for their high-end users, yet few can justify the high cost for all their users. Flexible multi-factor authentication enables organizations to issue the appropriate grade of credential for each user class from a single reusable infrastructure, and make adjustments as needed. Weak authentication, and inadequately protected identity data in on-line services are resulting in increasing instances of fraud. Organizations suffer reputational and financial losses and consumers loose confidence in on-line services. Organized criminal activity has just about started to move on-line, but is growing very fast. New attack vectors such as phishing have rapidly gained prominence in a matter of a few months. It is impossible to predict the nature of attack activity in 2006, let alone in 2007, 2008 … Enterprises are faced with uncertainty about the nature of real cyberattacks, yet must make funding decisions today on how to improve their existing authentication infrastructure. Therefore solutions that allow adjustment of credential strength as neededis are gaining prominence. The TriCipher Armored Credential System (TACS) provides a single platform that can issue and support a flexible range of credentials from a single infrastructure. The only system of its kind, the TACS Vault can be used to issue authentication credentials of many different types and can also serve as a vault for identity data (or encryption keys), providing a comprehensive solution to the problems of weak authentication and inadequately encrypted identity data. The authentication ladder (see Figure 1) shows TACS issued credentials in increasing order of strength as we go up the ladder. This flexibility is achieved due to the use of 3-key RSA as the underlying cryptographic engine for all forms of authentication. In 3-key RSA there are 2 private keys for each user, one which only the user knows and the other securely stored on the TACS Vault. (In contrast conventional 2-key RSA uses a single private key known only to the user.) Both private keys are used to generate partial signatures which are then combined to authenticate the user. Flexible multi-factor authentication is achieved by generating the user's personal private key from a variety of factors depending upon the credential strength.
In the simplest credential called Armored Passwords, the user's personal private key part is derived from a password. This eliminates the need to store encrypted passwords on the server and thereby eliminates password cracking by theft of these encrypted passwords. In Browser 2 Factor credentials the 2nd factor is stored in an encrypted cookie which comes to the server. Based on information in the cookie, an appropriate personalized "welcome message" is displayed to the user before they enter their password. The password and the cookie are then combined for two factor authentication. In Device 2 Factor credentials the user's PC (more than one can be registered) is used as a low cost and effective 2nd factor. The PC stores a non-exportable 2-key RSA private key which is cryptographically combined with the user's password to generate the user's personal private key. In Portable 2 Factor any removable device, ranging from USB memory sticks to iPods can be used as a convenient second factor. The approach is similar Device 2 Factor in that it combines a 2-key RSA private cryptographically with the user's password to generate the user's personal private key. The information on the portable device is protected both by the fact that the attacker does not have access to the key on the TACS Vault, as well as a special 'rolling key' which cryptographically encrypts the second factor. Armored Tokens add one-time passwords to the credential. The dynamic password travels from the client to the TACS Vault, which performs the verification. The protected channel from the client to the TACS Vault eliminates the man-in-the-middle attack to which one-time passwords are extremely vulnerable. For Smartcard-based credentials the private key stored in the smartcard (which is a conventional 2-key RSA private key) is used as the second factor, similar to the Device 2 Factor and Portable 2 Factor cases. This key never leaves the smartcard providing hardware protection for it. Most of the above 2 Factor solutions can be easily combined to form a 3 Factor credential. For instance Password + PC + USB Disk or Password + PC + Smartcard.
The TACS Vault itself is specially designed to afford a very high degree of assurance. It is protected using three layers of defenses: (i) it has a locked down, dedicated hardened OS, (ii) all system and user administration is strictly compartmentalized on least privilege, need to know, basis, and (iii) it uses FIPS 140-1 Level 2 rated cryptography. It is also highly scalable and fault tolerant, running as a set of 2 or 3 load-balanced and failover appliances. Finally it is a high assurance platform which can act as a secure storage facility to protect identity data such as credit card numbers. Enterprises can choose to either store identity data directly on the TACS Vault, or else can choose to encrypt data in place, and use the TACS Vault as a key management facility. The data is only available to authorized users after successful strong authentication. Link: Please contact: |
|||||||