This issue in pdf Subscription Archive: Next issue: January 2006 |
|
||||
Building a Stochastic Model for Security and Trust Assessment Evaluationby Karin Sallhammar, Svein Johan Knapskog and Bjarne Emil Helvik The ICT systems of today are complex inventions and we rely on their existence in almost all aspects of our everyday life. It is therefore crucial that they can provide the services we need whenever we require them. Due to the interconnection of networked systems, attacks are becoming increasingly sophisticated and can be performed remotely. To what degree can we trust that a system will perform its intended task in a secure and reliable manner? The new paradigms of ubiquitous computing and high capacity data transfer have opened up the Internet as the main area for information interchange and electronic commerce. Attacks against the computer networks used by modern society and economics for communication and finance can therefore threaten the economical and physical well-being of people and organizations. To allow continuous risk estimation of today´s ICT systems, there is an urgent need for models providing probabilistic measures of operational security. Stochastic Modelling
However, attacks may not always be well characterized by models of random nature. Most attackers will act with intent and will consider the possible consequences (satisfaction, profit and status versus the effort and risk of their actions) before they act. One of the remaining challenges is therefore how to incorporate intelligent attacker behaviour into the stochastic models. The Game Model
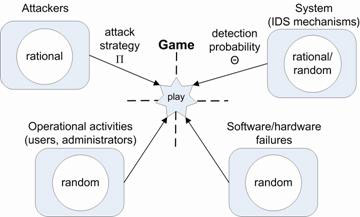
To incorporate intentional attacks in the model, the attacker behaviour must be predicted. By using a stochastic game model, we can compute the expected attacker behaviour for a number of different attacker profiles.
The game model in the figure is based on a reward/cost concept. This assumes that attackers will consider the reward of successful actions versus the possible cost of detection before they act, and that they will always try to maximize the expected outcome of the attack. The dynamics of the states of the stochastic games form a Markov chain, under the assumption that attackers, users and administrators do not change their behaviour over time. Having solved the stochastic game, the expected attacker behaviour can then be reflected in the transitions between states in the system model, by weighting the transition rates according to a probability distribution. In the final step, the corresponding stochastic process is used to calculate security measures of the system, in a similar manner to the common availability and reliability analysis of ICT systems. Previous research has shown that stochastic models can be used to model and analyse the trustworthiness of ICT systems in terms of both security and dependability attributes. Our current research indicates that game theory is a suitable tool for incorporating the expected attacker behaviour in such models. However, verifying the method’s ability to predict real-life attacks will require further research, including validation of the model against empirical data. Link: Please contact: |
||||