This issue in pdf Subscription Archive: Next issue: January 2006 |
|
|||||||
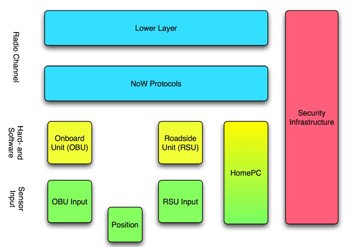
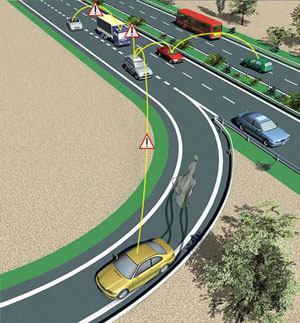
Trusted Network on Wheelsby Matthias Gerlach Vehicular ad hoc networks may become the largest ad hoc network ever deployed, and of fundamental importance for the safety and comfort of their users -the drivers and passengers. Clearly, deploying a revolutionary technology on such a large scale presents major challenges in the secure design of the system, its protocols and applications. Within Germany's nationally funded Network on Wheels (NoW) project, which started in June 2004, there is a dedicated group of experts from various companies and research institutes looking at potential attacks on such networks and devising methods and mechanisms to protect them. This is the first occasion that security considerations have been applied from the start of network development. This article provides some insight into the current and future work on security in the NoW project, and demonstrates the seriousness with which security and privacy are regarded. Vehicular Ad Hoc Networks The challenges in this new type of network are the short contact times between different mobile nodes, a far from ideal radio environment that includes large vehicles which obstruct the radio path, and the sheer size of the network. In addition, management of the network can no longer rely on ubiquitous infrastructure access, as ad hoc networks allow for infrastructure-independent operation. These restrictions of the network make the design of security mechanisms very challenging, and the fact that the system is under constant development does not make the process any easier. Security Requirements
The privacy of users is an important asset in public networks. Basically, privacy requires untraceability of actions to a user and unlinkability of the actions of a node. These must be provided by the applications as far as possible, and be inherent to the internal functionalities of the communication system. The communication system should give away as little information as possible that could be used to violate the privacy of the users. Finally, correctness in the security domain relates to secure communication. This boils down to the well-known security objectives of authenticity, freshness (which is, in fact authenticity in the time domain), integrity and non-repudiation. Another important aspect within such a system will be authorization in the different levels of the system, starting from the authorization to send messages on the radio interface to the use of certain application layer services provided by the network.
Approach in NoW Starting from general attacks such as the insertion of false messages, system denial of service and privacy violations, attacks can be refined using attack trees. Attack trees represent a hierarchical organization of an attacker's goals in AND and OR conjunctions, which become more detailed the deeper down the tree you go. Attack trees can also be used to assess the impact of a system's vulnerabilities, so as to decide where the priority of the work must be. Within the Security Working Group of NoW, we are currently constructing attack trees for a variety of applications using different services of the communication subsystem. Both the attack trees and mechanisms to secure the network will be published and discussed openly as they are finalized. In the Security Working Group of NoW, we believe that security mechanisms should be publicly scrutinized before they become part of the actual system. Links: Please contact: |
|||||||