This issue in pdf Subscription Archive: Next issue: January 2006 |
|
||||
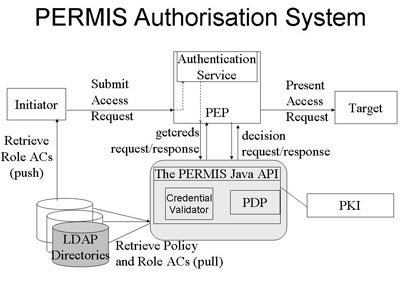
Security and Trust Management Extensions to the PERMIS X.509 Privilege Management Infrastructureby David ChadwickAuthorization in vitual organizations (VOs) and multi-organization federations is difficult to set up and manage. Having a pan-VO role- or attribute-based access control infrastructure can ease the burden, providing that trust relationships between the various entities can be safely managed. This is the problem domain that the PERMIS authorization system (www.openpermis.org) has been addressing for several years. Currently, three research projects are adding significant new capabilities to it, in the form of dynamic delegation of authority, separation of duties, and reputation management of the participants. The PERMIS Trust Model The SOA's policy, which follows the classical Role Based Access Control (RBAC) model, comprises two parts:
The RAP enables static delegation of authority because the SOA names one or more (possibly remotely located) managers who are trusted to assign roles. Since the names of these remote managers are included inside the digitally signed policy AC, they cannot be unknowingly tampered with; therefore PERMIS is able to trust these remote managers to assign X.509 role ACs to groups of users. Any role ACs that PERMIS is passed or retrieves in getcreds that do not conform to the RAP are simply discarded. In this way the SOA can be assured that his/her delegation policy is being rigorously enforced by PERMIS. Current Research Projects
DyCom is combing PERMIS with GRASP to create a fine-grained access control infrastructure for Grids, and is also adding separation of duties to the PERMIS trust model. Separation of duties will ensure that a user with mutually exclusive roles is not allowed to perform conflicting tasks. This requires PERMIS to keep a record of past and present authorized actions, so that future conflicting ones can be denied. In an offshoot of this project, we have developed a secure audit Web service (SAWS) as a general purpose audit tool. As part of the EC TrustCoM integrated project, we have built a reputation management system capable of recording the reputations of users (for example, as performed by eBay). The next step is to link this to the PERMIS decision engine so that access control decisions can be based on the current reputation of a user (which is related to their trustworthiness). Currently users are either trusted or not to access a target resource, based on their X.509 ACs. Once reputations are included in the decision-making however, users' permissions may be removed if their reputation drops below a certain value. In addition, the TrustCoM project is defining standard protocols for credential validation (ie calls to getcreds) and the making of policy decisions (ie calls to decision). It is likely that WS-TRUST and XACML respectively will be used for these. PERMIS will be enhanced to support these protocols once they have been finalized by the consortium. Link: Please contact: Richard Sinnott, (for DyVOSE), University of Kent, UK Damian Mac Randal (for DyCom), CCLRC, UK Theo Dimitrakos (for TrustCoM), BT, UK |
||||