|
|||
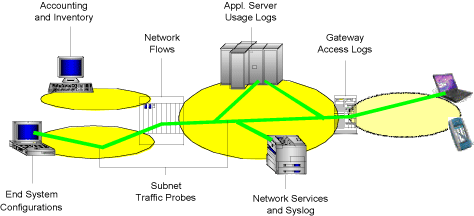
Tracking Assets and Vulnerabilities in Corporate Networksby Dieter Gantenbein In today's dynamic information society, organizations critically depend on the underlying computing infrastructure. Mobile users and computing devices add to the challenge. Business operations, intellectual property, and corporate value are quickly at risk. The IBM Zurich Research Laboratory has developed a tool called Intelligent Device Discovery (IDD) that collects information from all possible sources, computes an aggregate picture of assets, and categorizes their usage and vulnerabilities. Tracking computing devices as assets with usage, health, and vulnerability information facilitates the provision and maintenance of an efficient, optimized service. Recent incidents with viruses and worms appear to support this. In general, a precise understanding of the operational infrastructure is a key element of many corporate decisions. Examples also include the negotiation of outsourcing contracts, the planning of mergers and acquisitions, server consolidation and business optimization. Building an accurate inventory of computing assets in heterogeneous dynamic systems and networking environments is difficult, especially when only limited privileges are available and no prior device instrumentation has taken place. Classical methods for inventory and asset management quickly reach their limit in today's dynamic environments: Periodic physical inventories ('wall-to-wall') have the distinct advantage of identifying the actual location of devices but require costly human visits ('sneaker net') and cannot detect mobile, currently out-of-office equipment nor the existence and use of logical assets. Financial asset tracking, although an accepted process in its own right, cannot detect additional equipment brought into or accessing the resources of an organization. Periodic self-assessment questionnaires to be filled out by individual end users or their cost-center managers are another, often complementary approach. Apart from the human effort they require and the inaccurate, incomplete data they may contain, most forms pose questions the answers to which could easily be obtained from the infrastructure itself.
Well-managed computing infrastructures typically equip servers and end-user devices with software daemons to track the system's resources and health. There are many situations, however, in which these daemons cannot be relied upon. In many organizations, there are a fair number of devices that are brought in ad-hoc without appropriate instrumentation, for which instrumentation is not available, or on which instrumentation has been disabled. It therefore appears advisable to complement process and policy-based asset and security management with 'automatic sensors' to recalibrate the dynamic and heterogeneous environment. This is where IDD fits in. Scenarios How many old Windows systems with less than 512 MB of memory do we need to upgrade this geography? Where does this device with a strange MAC address come from? Which machines are unsafe, ie, without the latest patches and not protected by antivirus and security software? Computer A is a safe machine used by a secretarial employee on the mornings of four out of seven days a week. Computer B - perhaps a student-lab workstation - has many server ports open, is not completely safe, and is shared by users X, Y and Z. Some server has local unprotected databases and no screen password set. A portable device currently in office C has no hardware password set. And those rogue servers should either be turned off or turned into a policy-based operation. We may want to send e-mails to those employees whose machine configurations harbor discovered or accepted risks. Discovery provides the means to detect early potential exposures and track down the exact location of assets in violation of current policies. Information Sources Techniques Conclusions Link: Please contact: |
|||