This issue in pdf Subscription Archive: Next issue: January 2006 |
|
||||
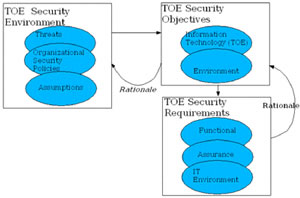
Bringing the Common Critera to Business Enterpriseby Christophe Ponsard, Philippe Massonet and Jean-François Molderez Security is a primary concern for companies, many of which are quickly becoming aware of it but are still ignorant of how to handle it correctly. The Common Criteria (CC) provides a systematic approach with a methodology and a set of reusable protection profiles. In practice however, they have proven difficult to adopt and costly to use. In order to overcome these obstacles, CETIC (Centre of Excellence in Information Technology and Communication) is promoting an adapted usage of CC, and has developed supporting tools based on an existing requirements-engineering toolkit. Information security has become a critical aspect in the operations of many companies, from multinationals to SMEs. Failing to address it adequately can have dramatic consequences: loss of access to data can freeze an organization, sensitive information might be sold to competitors, and so on. In an ever more connected world, ever more exposed to malicious users, many companies are exposed to such a painful experience before becoming aware of the importance of designing for security. Such design starts by correctly specifying what is to be protected, against what threat, and in which environment. Over the years, a number of standards that were developed separately finally converged to the ‘Common Criteria’ (CC), an internationally agreed method for gathering, organizing and assessing the security requirements for an IT product. CC provides a scale of eight evaluation assurance levels (EALs) in line with the effort and techniques required to develop a secure IT product. The resulting process is similar to a typical requirements engineering (RE) process (see figure). It includes an analysis of the environment, the definition of high-level objectives to address potential threats and their refinement into concrete requirements. Certification requires a strong rationale to be provided for the artefacts under evaluation.
Besides the fact that CC is an international standard, it is also based on sound RE practice and includes flexible adaptation mechanisms. Designers are free to reuse and/or adapt predefined requirements, or to add specific and customized requirements. They can also build requirements models at various abstraction levels, thus leaving details for later implementation stages. Connecting with Business Enterprise Based on discussions with Belgian companies of various sizes, CC was perceived as difficult to understand, learn and apply in the context of a small structure, and definitely not worth using for systems in which security is less critical. In order to overcome those difficulties, a number of improvements have been identified. For example, companies often ignore the fact that several protection profiles are already freely available; these can provide an exhaustive checklist of security requirements for various systems such as cash machine, firewalls, e-purse systems and so on. The conformance between the system and the profile can also be managed at the right assurance level, achieving a good balance between system criticality and available resources. It is also possible to apply only part of the process. This is the case in the Electronic Money System Security Objectives: based on a comprehensive risk analysis for e-money systems, this document develops a list of security objectives that should be fulfilled in order to cover these risks/threats in a given environment. An important part of the problem is also that security is a ‘vertical concern’, implying all system levels from hardware to middleware to software applications. A successful security design should therefore rely on an interdisciplinary approach, involving people from fields such as software quality, distributed systems and electronic systems, the three main fields in which CETIC is active. Finally, tool support is also crucial. So far there exist few tools for the Common Criteria (and more generally in the RE field) that have a real methodological support. The most widely used tool is a word processor, possibly complemented with a traceability tool. An ideal tool should provide a rich meta-model capturing relevant security concepts such as the environment, threats, agents (user or malicious), security objectives and requirements. It should support the CC library, query it and provide operations (refinement, iteration, selection etc) on it. Most importantly, it should capture the rationale between all the required CC artefacts in order to automate document generation as far as possible. Further Work CETIC is currently working on this area in collaboration with Belgian companies and universities, in the context of various European projects. Based on our expertise in requirements engineering for critical systems and in tool development, CETIC is working on the specification of domain-specific protection profiles and the development of an adapted tool support to ease the use of the Common Criteria. Security in domains such as the GRID and ambient intelligence are being investigated, as well as the application of CC at a high assurance level with the use of formal methods. Link: Please contact: |
||||