This issue in pdf Subscription Archive: Next issue: January 2006 |
|
|||||||
Interactive Access Control and Trust Negotiation for Autonomic Communicationby Hristo Koshutanski and Fabio Massacci Recent advances in Internet technology and globalization of peer-to-peer communications offer organizations and individuals an open environment for rapid and dynamic resource integration. In such an environment, federations of heterogeneous systems are formed with no central authority and no unified security infrastructure. Considering this level of openness each server is responsible for the management and enforcement of its own security policies with a high degree of autonomy. Dynamic coalitions and autonomic communication add new challenges: a truly autonomic network is born when nodes are no longer within the boundary of a single enterprise, which could deploy its policies on each and every node and guarantee interoperability. An autonomic network is characterized by the self-management and self-configuration of its constituent nodes. In an autonomic network, nodes are partners that offer services and lightly integrate their efforts into one (hopefully coherent) network. Policy-based network access and management already requires a paradigm shift in the access control mechanism: from identity-based access control to trust management and negotiation, but even this is not enough for cross-organizational autonomic communication. In an autonomic communication scenario, a client may have all the necessary credentials to access a service but may be unaware of this. Equally, it is unrealistic to assume that servers will publish their security policies on the Web so that clients can perform policy combinations and evaluations themselves. Rather, it should be possible for a server to ask a client, on the fly, for additional credentials: the client may then choose whether or not to disclose them. The server then re-evaluates the client’s request taking the newly submitted credentials into consideration, and iterates the process until a final decision (of ‘grant’ or ‘deny’) is reached. We call this modality interactive access control. While some of these challenges can be solved by using policy-based self-management of networks, this is not universally the case. Indeed, if we abstract away the details of the policy implementation, we can observe that the only reasoning service that is actually used by policy-based self-management approaches is deduction: given a policy and a set of additional facts, find out all consequences (actions or obligations) of the policy and the facts. We simply look at whether granting the request can be deduced from the policy and the current facts. Autonomic communication needs another reasoning service: abduction. Loosely speaking, we could say that abduction is deduction in reverse: given a policy and a request to access a service, we want to know what credentials/events are missing that would grant access. The contribution of the framework is in the way we bootstrap from the basic reasoning services of deduction, abduction and consistency checking, a comprehensive interactive access-control algorithm that computes on the fly the missing credentials needed for a client to get access. We extended the algorithm to cope with arbitrary access policies so that in cases of inconsistency it performs a recovery step and finds a set of excessing credentials banning the client to get a solution for the desired resource. Following this, a strengthened version of the algorithm is devised that is resistant to DoS attacks. We have modelled a fully fledged access-control framework and shown its correctness and completeness.
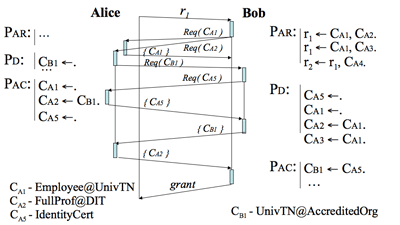
Based on the interactive access-control algorithm, we introduce a trust negotiation protocol that runs on both client- and server-sides. It automatically interoperates and negotiates missing credentials until either a final decision of ‘grant’ is taken and the negotiation is successfully completed, or one of the parties fails to negotiate the requirements and the service request is denied. Figure 2 shows a message-flow example of the negotiation protocol.
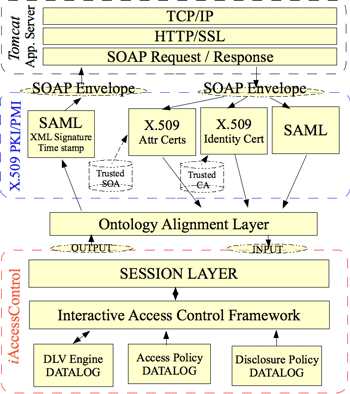
We have implemented the interactive access-control modality as a Web Service. For this purpose we used X.509 PKI/PMI and OASIS SAML standards as a unified way of conveying credentials and defining authorization statements respectively. We integrated the two standards with the W3C SOAP protocol so that our access control engine can be used and invoked in a platform-independent manner. We have done a Java wrapper for the DLV system that implements the interactive access-control algorithm. The DLV system is used as a core engine of the basic functionalities of deduction, abduction and consistency checking. The architecture of the access control engine is shown in the Figure 1. Future work will look at characterizing the complexity of the framework and extending it to cope with stateful systems and especially with the open issues of revocation of credentials. Links: Please contact: |
|||||||