This issue in pdf Subscription Archive: Next issue: January 2006 |
|
||||
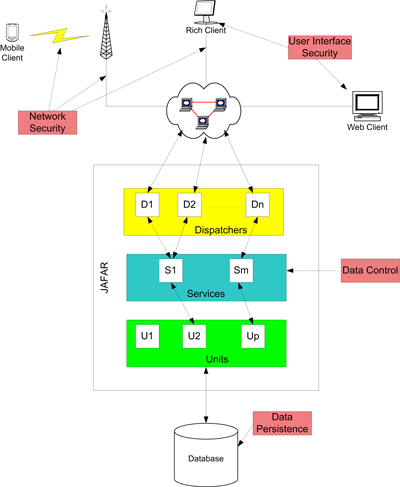
Securing JAFAR - An Architectural Framework for E-Commerce Applicationsby Nicolas Guelfi, Cédric Pruski, Jan Reimen and Paul Sterges Security is the key to the success of e-commerce applications. In the context of the 'FIDJI' project, the Software Engineering Competence Center (SE2C) at the University of Luxembourg has developed JAFAR, a J2EE (Java 2 Platform, Enterprise Edition) architectural framework for the development of secure e-commerce applications. Research is now focusing on the various security problems that are directly linked to the use and development of such applications. Since the early nineties and the advent of distributed e-commerce, computer science has been confronted with problems related to security, in both the exchange and server-side handling of data. The key to success for e-commerce applications resides in gaining the trust of potential users. Applications must therefore be developed in order to offer adequate levels of security. The ADS (Architecture Engineering for Dependable Distributed Systems) team of the SE2C is interested in three major problems relating to security and trust management in the development and use of distributed e-commerce applications.
First, in the eyes of users, data confidentiality during an exchange between the client application and the server constitutes the most critical point of security. This phenomenon, which remains purely a network problem, increased in importance with the arrival of third-generation telecommunications networks and the appearance of the mobile commerce (m-commerce) paradigm. The use of an architectural framework such as JAFAR allows the developers of distributed applications to take into account and to more easily solve, at the software level, this problem of data exchange. This is managed in particular through the use of security solutions already implemented in the heart of the framework (eg communication interfaces supporting the TLS protocol, the use of certificates to encrypt the data etc). In addition, where the level of confidentiality demands it, the framework is enriched by the development of other components that integrate more powerful means of encryption. Security certificates also are important to authenticate the e-commerce site to the users. We are currently studying the various security solutions that can be used in the context of e-commerce and integrated in JAFAR, in particular solutions over UMTS networks. Second, both the persistence and the availability of data are significant points in the success of e-commerce applications. Indeed, considering the company Amazon, an outage of its Web interface would have a very significant effect on its sales turnover. Thus, the applications must be designed in order to prevent remote attacks such as denial of service attacks, which target the availability of resources. During the development of JAFAR, we have studied the various possibilities for detecting this type of attack, as well as the measures to be taken when a major resource is no longer available. In particular, we are working on the decentralized aspect of the resources in order to reduce as far as possible the length of time for which they are unavailable. However, we also envisage integrating the adaptation and resilience aspects of the system in the near future, by means of other projects such as CORRECT, privileging the fault-tolerance aspect, or new projects awaiting validation from the European commission. Lastly, since storage security is relative to the business application and its supporting storage infrastructure, a risk mitigation methodology is a sound way to strengthen storage availability, reliability and privacy. This is why storage of and access to stored data are the final two significant points that influence the design of e-commerce applications. The layer architecture of JAFAR is conceived in a rigorous way and determines the permissions granted to users after their identification. In addition, JAFAR was developed in order to offer a maximum of services to users while reducing the number of interfaces that make it possible to seize information or introduce erroneous data. The latter particularly includes code that is interpretable by the system, such as SQL or HTML, which can have disastrous effects on stored data. We are studying ways to define security rules which will be checked at run-time and which can be changed on a production system to react to observed patterns of abuse. Moreover, JAFAR integrates a module making it possible to rigorously control the data to be stored by detecting possible pieces of malicious code. Links: Please contact: |
||||