This issue in pdf Subscription Archive: Next issue: January 2006 |
|
||||
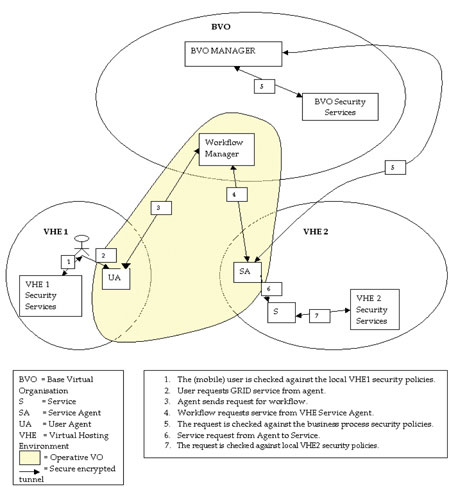
An Akogrimo Approach to Securing Virtual Organizations within Mobile GRID Computing Environmentsby Thomas Kirkham, Giuseppe Cirillo, Julian Gallop, Damian Mac Randal, Brian Ritchie and Pierluigi Ritrovato The Akogrimo Project (EU FP6-IST, 2004 to 2007) was introduced in a previous article, 'The Grid Goes Mobile' in ERCIM News (Issue 59). Akogrimo is aiming to radically advance the pervasiveness of Grid computing across Europe. To achieve this goal, and in addition to embracing layers and technologies which are intended to make up the so-called next-generation Grids (eg knowledge-related and semantics-driven Web services), Akogrimo aims to design and prototype a blueprint of a next-generation Grid that exploits and closely cooperates with evolving mobile Internet infrastructures based on IPv6. In this article, initial higher-level work on the security of virtual organizations and future plans for work in the security area are discussed. Mobile Dynamic Virtual Organizations (MDVO) In Akogrimo, mobility is clearly a key concern. Since the VOs are both mobile and dynamic, several security issues are raised ranging from connection insecurity (wireless or otherwise) to Authentication, Authorization and Accounting (AAA) challenges. These security problems are present in particular during service discovery and re-discovery, since mobile services are prone to loss of connection, changes in bandwidth and so on. Operative Virtual Organisations (OpVO)
The figure shows a service able to operate within VHE2, a Virtual Hosting Environment, wrapped by a service agent (SA), and able to be invoked by a workflow in the OpVO. Security is handled in the VHE where the service resides and also in the Base VO where the service is registered. The Base VO is central to the model and has the power to create and destroy an OpVO. This allows the existence of a hierarchy, the apex of which is a central point of security and policy enforcement for the workflow. Direct communication should not be possible between entities (eg users, services, resources etc) that belong to different administration domains, without going through the Base VO's security services. The execution of services within the OpVO and VHE reduces the workload on the Base VO, and it can be argued that this reduces the potential of a security breach occurring within the main Base VO, which could be running multiple OpVOs. During workflow execution the Base VO in the model is largely used as a repository of VHE service details and security policy. The Workflow Manager links the VHEs to the Base VO for the purpose of discovery and authorization during the creation of an OpVO. This link calls services located in the VHEs by looking into the Base VO's service registry. As services are discovered and brought into the OpVO they are authenticated and granted access via the secure exchange of tokens issued by the Base VO. If a service drops out or loses its connection after discovery, the workflow manager has the ability to send a request from the OpVO for a new service to be used; in this case the discovery and authentication process from the Base VO will be repeated. This re-authentication will help prevent security breaches such as 'man in the middle' attacks, which are popular on wireless connections. In addition, all traffic from the OpVO to the Base VO will be via an encrypted Web Service Secure Conversation link. Conclusion and Future Work Links: Please contact: |
||||