|
ERCIM News No.49, April 2002
|
SMM - Assessing a Company's IT Security
by Holger Kurrek
Are you investing your money for IT security in a holistic solution or are you guarding your frontage, while leaving the back doors open? The Fraunhofer Institute for Software and Systems Engineering (ISST) has developed a 'Security Maturity Model' (SMM) to assess a company's IT security.
Security is a matter of trust. Today, an enterprise cannot afford to lose its reputation and consequently its clients because of insufficient system security. IT security measures should therefore be transparent, complex and purposeful, but also easy to implement and cost-effective. The question is: how can we accurately define IT security? Since IT systems are strongly influenced by human behaviour, the answer lies far beyond purely technical solutions. The Fraunhofer ISST assesses the 'maturity' of a company's IT security with its specially developed'Security Maturity Model'. After determining the current safety level, a concept is composed defining all the measures necessary to reach the next level. With this step-by-step model, the expected expenditure can be calculated more thoroughly. Through a goal-directed deployment of all means (within a level), even investments will become economically efficient.
Analysis
The analysis examines technical as well as organisational components and their integration in the corporate culture. The latter two fields have been minimally considered by previous procedures. Therefore, SMM offers a real opportunity for assessment.
Technology
All possible components are tested on their state of technological development and effective usage. The focal points of this assessment are capacity, quality and integration. Costs of purchase and operation as well as future capacity are also considered.
Organization
Technology is, however, only effective if organisational concepts use it effectively. Besides the definition of an IT security policy and its corresponding responsibilities, the focus of interest lies in a holistic IT security concept. Connections with suppliers, customers and partners are of central importance. We therefore examine particularly the contracts and the stated parameters in the Service Level Agreements. Furthermore, we will assess the precise predefinitions of authorisations and responsibilities.
Corporate Culture
Technical and organisational measures must be deeply integrated into the corporate culture if a satisfactory effect is to be produced. Only decisive daily behaviour from both employees and management, also understood in the long term as a quality assurance process, will guarantee success. An atmosphere of attention and care can improve IT security considerably and can be very cost-effective. This is not only an assessment of IT experts and people in charge of IT security, but of all employees working with IT applications.
Apart from psychological aspects, such as the sense of responsibility, we also assess existing know-how and qualifications. A significant factor is purposeful staff development and its appropriate planning.
Assessment
The results of the analysis are then evaluated. Rather than being looked at separately, the various factors are observed in such a way as to take into account how they combine with each other. This allows us to accurately determine the current level of security and ensure the appropriate procedure. Thus, one can reconstruct how this particular level has been attained. Existing measures and actions necessary to reach the next level will also be identified to enable a goal-directed investment in those components which are still missing. Often large investments into technical components can be significantly reduced though organisational measures and the normal and necessary development of corporate culture.
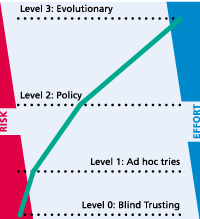 |
The four levels of the Security Maturity Model. |
The figure shows the four levels of the model. Starting point is level 0 'blind trust', ie, the complete renunciation of IT security. By the use of minimal means, level 1 can be reached. A coordination of measures leads to level 2. The highest level can be attained through the usage of continuous processes (in detail these levels are much more complex and are specified in comprehensive measure catalogues).
Advantages
Using SMM is a fast way to identify the current state of a company's IT security. A cost-effective realisation is made possible through the optimisation of expenditure and concentration on the necessary focal points. With the bundling of all measures, synergies arise. Thus, goals are reached faster and expenditure is simultaneously reduced. The comprehensive model avoids discrepancies within the measures, which could otherwise cause gaps in IT security. The identification of the goals of the following level allows a strategic approach and improves financial control.
Services
Based on SMM, the Fraunhofer ISST offers the following services:
- evaluation of the current situation, eg during Technical Due Diligence
- formulation of measures to increase IT security
- quality assurance attendance of IT security measures.
To realise the measures, the Fraunhofer ISST relies on a procedural model and reference architectures.
Outlook
SMM is constantly being developed, since customers regularly test it in practice (small businesses and also large-scale enterprises and public administrations). In this way, not only is the analysis refined but the measures are also repeatedly rated on the current state of technology and can thus keep pace with its highly dynamic development.
An important focus is the comparability with other companies, not only to classify the competition but also to attain a continuously high level of security between partners. All developments will be added to the procedural model and reference architectures. Collaborations also exist between the institutes of the Fraunhofer-Gesellschaft, especially in the field of encryption and its necessary infrastructures (Public Key Infrastructure, PKI).
Links:
FhG-ISST: http://www.isst.fhg.de/
Please contact:
Holger Kurrek, FhG-ISST
Tel: +49 30 243 06 355
E-mail: holger.kurrek@isst.fhg.de
